Multiple Open URL Redirection Vulnerability on Facebook worth $1500
Hello,
Facebook is the first bug bounty program which I have participated in the initial stage of Bug Hunting. Within few days, I've reported multiple open URL redirection Vulnerabilities to facebook and it became duplicate. I still remember that it was my first valid finding I have identified and it became duplicate. Later, I dug more into the Facebook Developers Page and come with another few more tricky Open URL redirection vulnerabilities.Fortunately, Facebook accepted my finding and patched the security vulnerability with the bug bountry reward of $1500.
Observation
Facebook Dialogs provide a simple, consistent interface to provide social functionality to people using your apps. Dialogs do not require any additional permissions because they require someone to directly interact with them. Dialogs can be used by your application in several contexts: in a website or mobile web app, within native iOS and native Android applications, or in a game on Facebook.com (Excerpt from TAF )
Due to improper Server Side validation, Open URL Redirection Vulnerability exists on mentioned Facebook Dialogs.An attacker can frame a URL with malicious website in the User Controllable Facebook Dialogs input, Facebook server will process the request and users will be redirected to different website in an unsafe way.
- Send Dialog
- Pagetab Dialog
- Apprequest Dialog
Proof of Concept
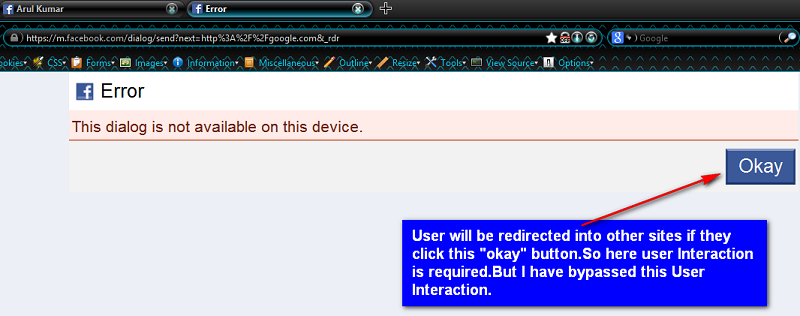
Whenever victim clicks any one of the vulnerable links they will get an error with submit button and if they click the okay button they will be redirected to google.
https://m.facebook.com/dialog/send?next=https://google.com
https://m.facebook.com/dialog/pagetab?next=https://google.com
https://m.facebook.com/dialog/apprequests?next=https://google.com
Initial Response from Facebook
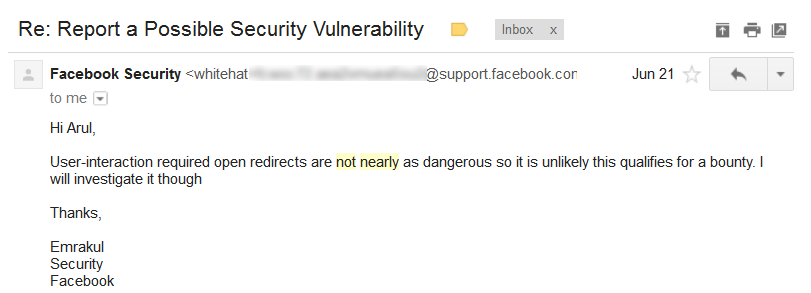
As it requires user interaction to perform open URL redirection, Facebook Team comes up with some negative response which may not qualify for bounty
Bypassing User Interaction
Now,It's time to bypass the user interaction.

I started Analysing the HTML Source of the Page and noticed that submit button can be user controllable. So, I have added another parameter error_ok in URL with some value.Luckily, Facebook server processed the Open URL Redirection request without User interaction.
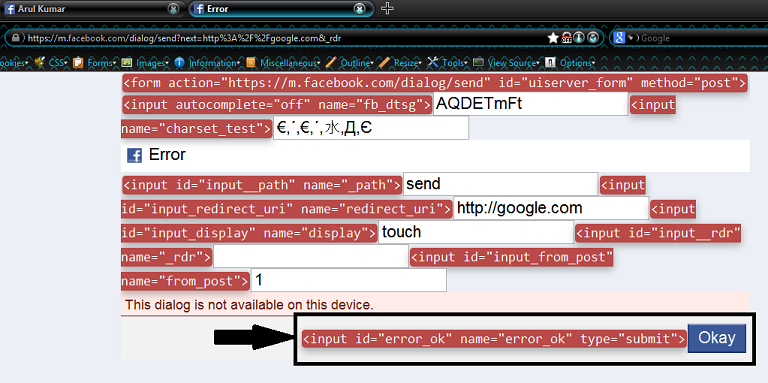
https://m.facebook.com/dialog/send?next=https://google.com&error_ok=blah
https://m.facebook.com/dialog/pagetab?next=https://google.com&error_ok=blah
https://m.facebook.com/dialog/apprequests?next=https://google.com&error_ok=blah
So,I've wrote regarding this bypass technique to facebook team and got some positive response from facebook this time.
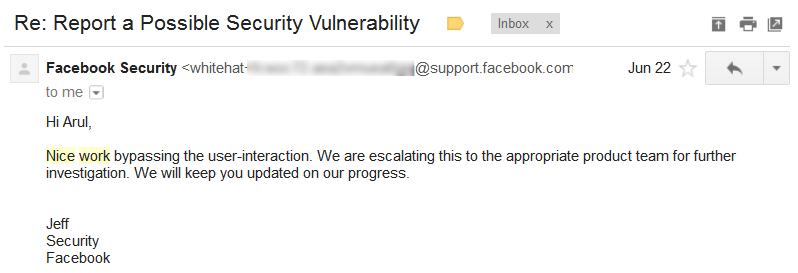
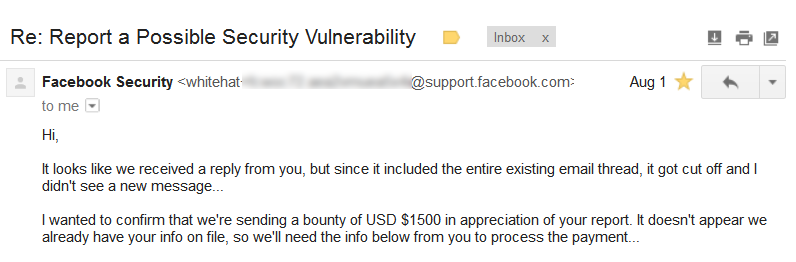
Bounty Confirmation
Video POC [Rewarded]
Video POC [Duplicate]
Hall of Fame