Multiple Open URL Redirection Vulnerability on Facebook worth $1500
Hello Everyone,
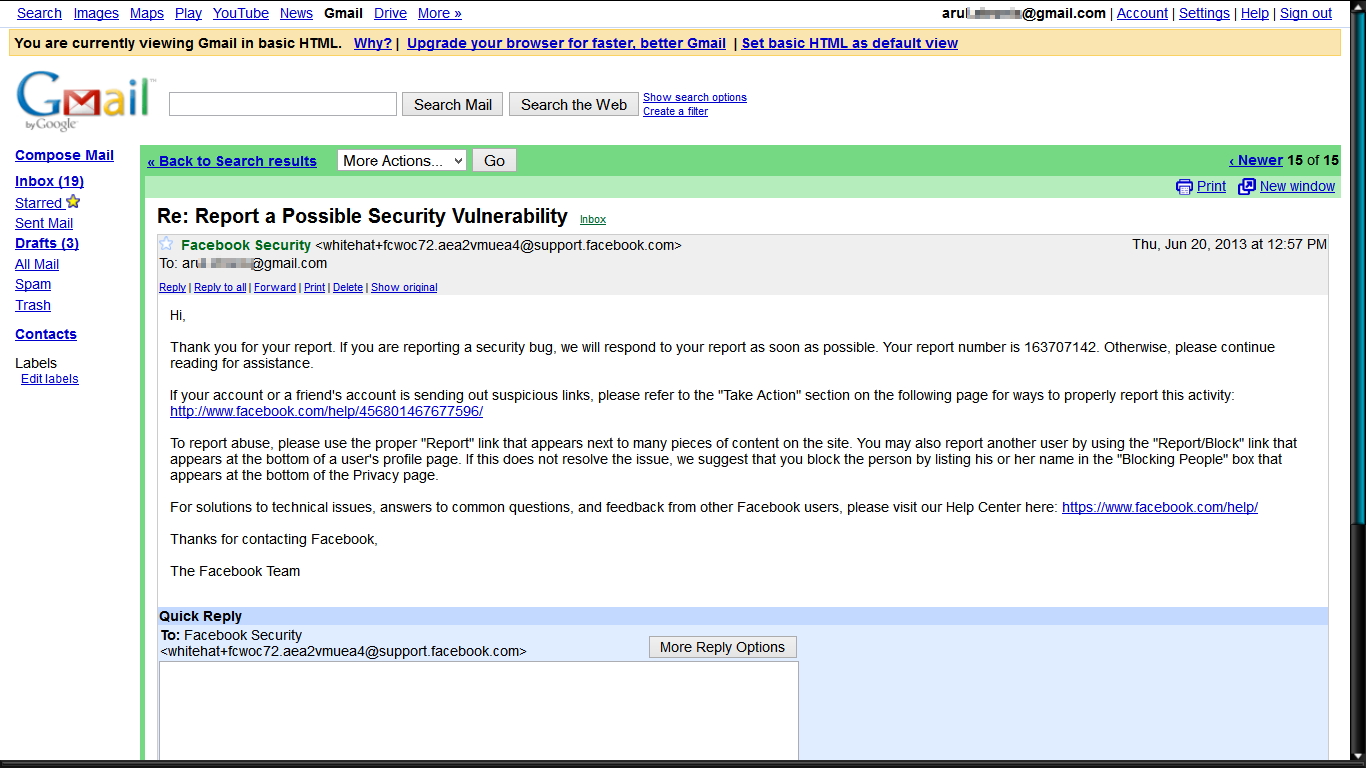
Facebook was the first bug bounty program in which I participated during the initial stage of my Bug Hunting journey. Within a few days, I reported multiple open URL redirection vulnerabilities to Facebook, but they were marked as duplicates. I still remember that it was my first valid finding, and although it became a duplicate, I continued digging deeper into the Facebook Developers Page. I discovered several more tricky open URL redirection vulnerabilities. Fortunately, Facebook accepted my findings and patched the security vulnerability with a bug bounty reward of $1500.
Observation
Facebook Dialogs provide a simple and consistent interface for developers to integrate social functionality into their applications. Dialogs do not require any additional permissions because they require direct user interaction. Dialogs can be used in several contexts: on websites or mobile web apps, within native iOS and native Android applications, or in games on Facebook.com.
Due to improper server-side validation, an Open URL Redirection vulnerability existed in the mentioned Facebook Dialogs. An attacker could craft a URL with a malicious website in the user-controllable Facebook Dialogs input field. Facebook’s server would process the request and redirect users to a different website in an unsafe manner.
Vulnerable Dialogs:
- Send Dialog
- Page Tab Dialog
- App Request Dialog
Proof of Concept
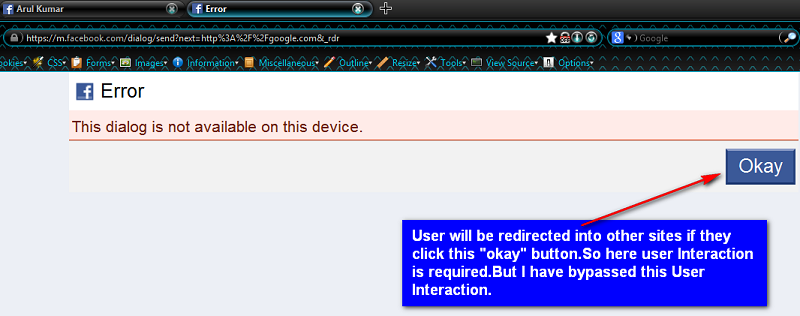
When a victim clicked any one of the vulnerable links, they would receive an error message with a submit button. Upon clicking the okay button, they would be redirected to Google.
1
2
3
https://m.facebook.com/dialog/send?next=https://google.com
https://m.facebook.com/dialog/pagetab?next=https://google.com
https://m.facebook.com/dialog/apprequests?next=https://google.com
Initial Response from Facebook
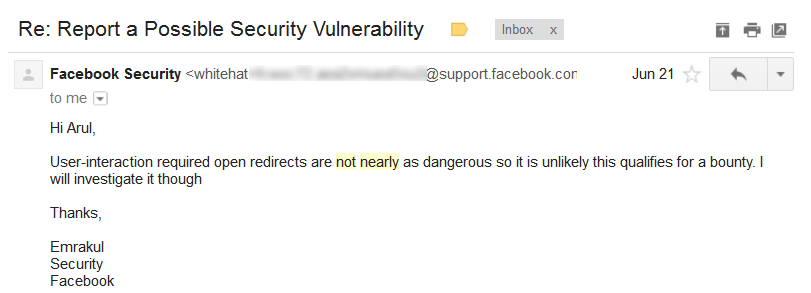
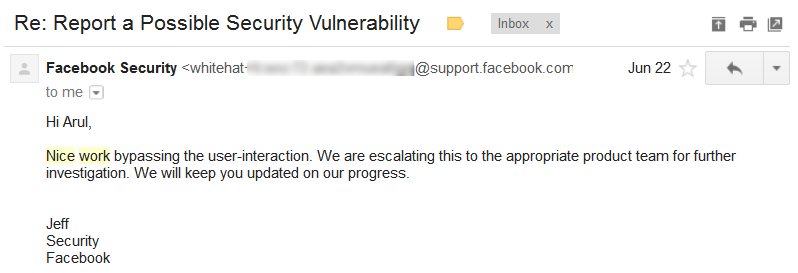
Since the vulnerability required user interaction to perform the open URL redirection, the Facebook Team initially responded negatively, suggesting it might not qualify for a bounty.
Bypassing User Interaction
Now came the challenge: bypassing the user interaction requirement.
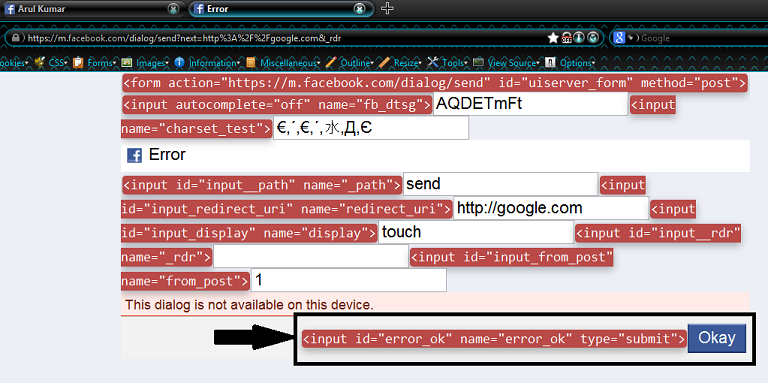
I began analyzing the HTML source code of the page and discovered that the submit button could be made user-controllable. I added another parameter, error_ok, to the URL with an arbitrary value. Fortunately, Facebook’s server processed the Open URL Redirection request without requiring user interaction.
Updated POC URLs (with user interaction bypass):
1
2
3
https://m.facebook.com/dialog/send?next=https://google.com&error_ok=blah
https://m.facebook.com/dialog/pagetab?next=https://google.com&error_ok=blah
https://m.facebook.com/dialog/apprequests?next=https://google.com&error_ok=blah
I reported this bypass technique to the Facebook team and received a positive response this time.
Bounty Confirmation
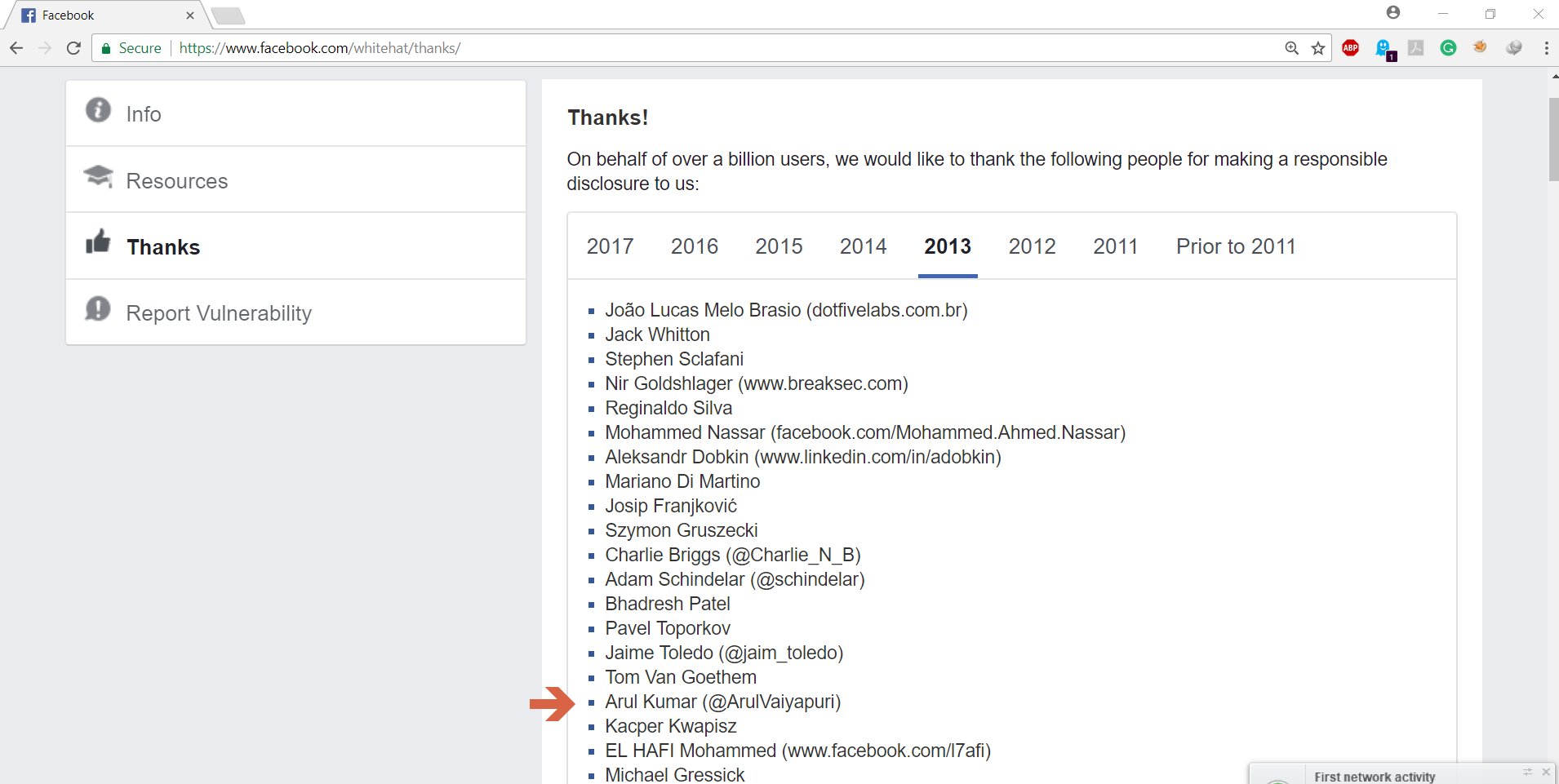
Hall of Fame
Video POC
Tags: Vulnerability · Facebook · Bug Bounty · Open Redirection