React2Shell (CVE-2025-55182) — Docker Vulnerable Lab
React2Shell (CVE-2025-55182) — Docker Vulnerable Lab
This short post shows how to run the React2Shell vulnerable lab locally using Docker. The instructions are simple and repeatable — ideal for spinning up a disposable environment for learning or testing CVE-2025-55182.
Important: Run this lab only in isolated environments you control (local VM or disposable container). Do NOT target systems you do not own or lack explicit permission to test.
Quick Steps
- Clone the lab repository from GitHub.
- Build the Docker image (or pull the published image).
- Run the container and open the app at http://localhost:3000
Clone the repository
Open a terminal and run:
1
2
git clone https://github.com/subzer0x0/React2Shell.git
cd React2Shell
Option A — Build from source (recommended for development)
Build the Docker image locally and run it:
1
2
docker build -t react2shell:latest .
docker run --rm -p 3000:3000 react2shell:latest
Then open: http://localhost:3000
Notes:
- The container binds port
3000on the host. If that port is in use, change the left side of-p(for example-p 8080:3000).
Option B — Pull prebuilt image (fast)
If you prefer to use the published image from Docker Hub, pull and run it:
1
2
docker pull arulkumarv/react2shell:v1
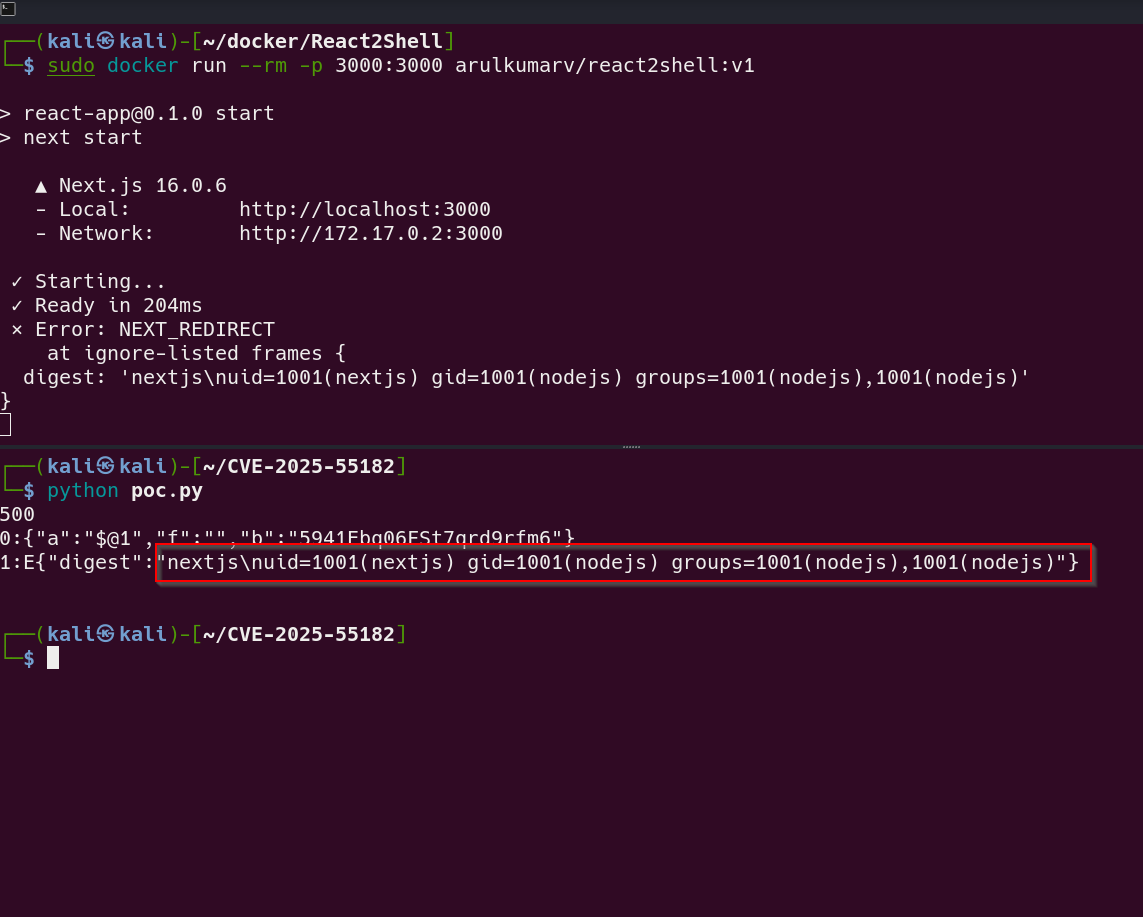
docker run --rm -p 3000:3000 arulkumarv/react2shell:v1
🔬 Exploit Proof‑of‑Concept (PoC)
A public PoC related to CVE-2025-55182 is available at msanft/CVE-2025-55182.
To fetch and run the PoC locally (only in an isolated lab):
1
2
3
git clone https://github.com/msanft/CVE-2025-55182
cd CVE-2025-55182
python poc.py
Additional resources
This post is licensed under CC BY 4.0 by the author.